Cybersecurity has moved from the back room to Congress, and from trade journals to mainstream news. In the public sector — Civilian, Defense, Intelligence Community, state government and education — CIOs must now put cybersecurity at the top of their priority list. Budgets are as tight as ever, so they must maximize the value of each expenditure, while complying with a maze of regulations, laws, and frameworks.
TD SYNNEX Public Sector understands these challenges, and the speed of change in technology making them harder every day. TD SYNNEX Public Sector sees security as foundations + innovation: a strong security and IT infrastructure lays the groundwork for leveraging innovative technologies that can outrun the bad actors. Our client offerings can strengthen your current security posture, and look ahead to new solutions that make our adversaries scramble to keep pace.
Our Approach
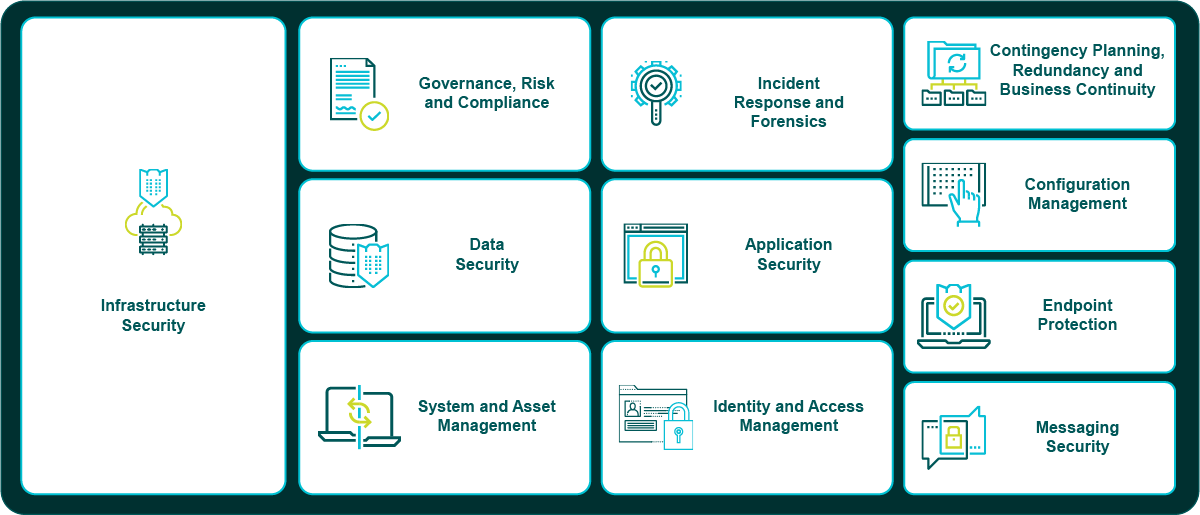
TD SYNNEX Public Sector understands the complexity of cybersecurity, which affects nearly every aspect of technology. To simplify matters, we boil down cyber into 13 categories; here’s the breakdown.
Application Security
To protect applications, write them securely.TD SYNNEX Public Sector's line includes tools and services to assist in secure application development at all phases of the development life cycle.
Even the most secure applications still need protection after deployment, so TD SYNNEX Public Sector also has a wealth of external systems and software to protect applications in production.
Configuration Management
Consistent device and application configuration is essential for strong security. This task is becoming increasingly difficult as users bring more devices to the network, applications and systems move to the cloud, and IOT devices proliferate.
TD SYNNEX Public Sector provides the tools you need to ensure consistent and up-to-date configuration of all types of devices and systems in your network.
Contingency Planning, Redundancy, & Business Continuity
Most organizations accept that bad actors will eventually compromise their network or critical systems. Consequently, it is essential to deploy tools for that:
- provide, system and data redundancy
- monitor and prevent denial-of-service DoS or DDoS) attacks,
- and ensure that you can operate even while recovering from a breach.
TD SYNNEX Public Sector's clients offer robust capabilities to help you recover, and get back to the mission ASAP.
Data Security
Ultimately, security is all about protecting data. Data security includes data encryption, monitoring data flows, detecting and preventing unauthorized changes, to all data -- at rest, in motion, or in use. TD SYNNEX Public Sector's robust line of security offerings cover all types of data, in all three scenarios.
Endpoint Protection
In the past, endpoint protection systems were virus detection programs that used signatures to identify malicious files. As attacks grew in sophistication, endpoint protection had to keep pace, to detect and neutralize "zero day" (brand new) attacks, and even to deal with attacks that don’t use files at all. TD SYNNEX Public Sector stays current with these trends, and our line of endpoint protection products offers state-of-the-art protection.
Governance, Risk, and Compliance
Government security programs spend much of their budget on compliance with laws, regulations, and policies. Too often, compliance does not equate to security. Consequently, TD SYNNEX Public Sector provides a line of products to automate or facilitate compliance. We also map our product line to specific compliance regimes, such as NIST 800-53 and the Cybersecurity Framework.
Identity and Access Management (IAM)
This is the art and science of ensuring that a user is who they say they are, ensuring that they have the right level of access to data, and that access is both convenient and secure.
TD SYNNEX Public Sector’s IAM offerings include:
- management and provisioning of user IDs and credentials
- privileged access management
- single sign-on,(SSO),
- and management of tools such as hardware and software tokens
Incident Response and Forensics (IR)
TD SYNNEX Public Sector’s IR systems respond to breaches automatically and enable security staff to react effectively to intrusions. Response capabilities include gathering and analysis of evidence for attribution, remediation of compromised systems, and automated incident reporting.
Infrastructure Security
Infrastructure Security includes almost any type of device or system that protects an organization’s infrastructure. The list includes devices such as:
- firewalls and next-generation firewalls
- electronic mail gateways
- network access control (NAC) systems
- intrusion detection/prevention systems (IDS/IPS)
- Web Application Firewalls (WAFS)
- and host-based intrusion detection systems (HIDS)
and technologies such as: - DDoS Monitoring and mitigation
- Software-defined Perimeter
- DNS Protection
TD SYNNEX Public Sector partners with clients who provide state-of-the-art systems and software in all of these areas.
Messaging Security
Phishing — deceptive e-mail that lures a victim into installing malware on their system — remains the most common mode of attack. Security of messaging systems in general and e-mail systems in particular is extremely important. These systems can block advanced threats and suspected malware to a sandbox for analysis, detonation, and risk scoring. They can also analyze file attachments and URLs, and act appropriately to ensure these threats cause no harm.
TD SYNNEX Public Sector has a wide range of messaging security solutions to guard against intrusions via messaging and e-mail systems.
System and Asset Management
It is impossible to secure unidentified assets. TD SYNNEX Public Sector's system and asset management products establish a baseline inventory essential for nearly any further security activities, and can ensure that all devices are secure.