Illumio enables organizations to realize a future without high-profile breaches by providing visibility, segmentation, and control of all network communications across any data center or cloud.
Founded in 2013, the world’s largest enterprises, including Morgan Stanley, BNP Paribas, Salesforce, and Oracle NetSuite, trust Illumio to reduce cyber risk.
Learn more at https://www.illumio.com/what-we-do.
Federal Certifications

A Leader in Zero Trust
 Illumio was founded on the principle of Zero Trust and dubbed the top current offering for Zero Trust in The Forrester Wave™: Zero Trust eXtended Ecosystem Platform Providers, Q4 2019, receiving the highest scores in:
Illumio was founded on the principle of Zero Trust and dubbed the top current offering for Zero Trust in The Forrester Wave™: Zero Trust eXtended Ecosystem Platform Providers, Q4 2019, receiving the highest scores in:
- Workload security
- Visibility and analytics
- Automation and orchestration
- Manageability and usability
- APIs
- Vision and strategy
- Advocacy
Beyond the Hype: Conversations on Mobilizing Zero Trust - featuring Chase Cunningham, Forrester principal analyst serving security & risk professionals, and PJ Kirner, Illumio CTO and co-founder
Adaptive Security Platform (ASP)
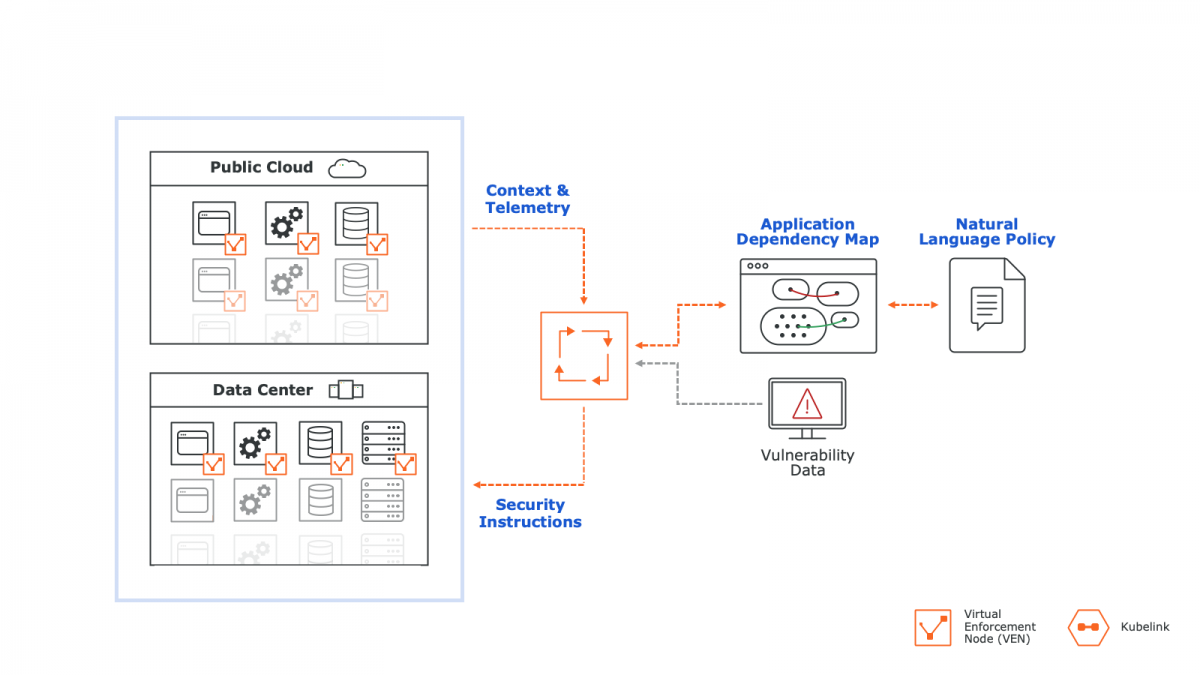
Illumio ASP is uniquely designed to enable you to use the enforcement points that already exist in your infrastructure to improve your data center and cloud security. No additional hardware or re-architecting your network.
Illumio ASP Architecture
The Virtual Enforcement Node (VEN) is a lightweight agent that sends and receives information, programs pre-existing enforcement points, and detects policy violations.
Features

Illumination
A real-time application dependency map that shows you how apps are communicating.

Policy Generator
Create optimal segmentation policies in minutes.

Explorer
Search and analyze historical records of traffic between workloads.

SecureConnect
Protect data in transit and execute workload-to-workload encryption.
Vulnerability Maps
See which applications are connecting to vulnerable ports in real time.

Segmentation Templates
Instantly secure critical off-the-shelf applications with tried-and-tested templates.
Here are the primary ways customers use Illumio.
- Forrester Wave: Zero Trust eXtended Ecosystem Providers, 4Q2019
- Solution Brief: Illumio ASP and NIST CSF
- Datasheet: Illumio ASP for Federal
- E-Book: Secure Beyond Breach
- Webinar: Illumio 3-Stage Zero Trust Plan
- Webinar: Fire Your Firewall
- Webinar: Webinar: How and Why to Decouple Security from Your SDN
- White Paper: Securing High Value Assets in the Federal Sector
- White Paper: How to Build a Micro-Segmentation Strategy
- White Paper: Decoupling Security from the Network
- Infographic: Why is Illumio Better than a Firewall?
- Illumio Design Guide
The Evolution of Segmentation
| Contract Name | Contract Number | Sector | State |
|---|---|---|---|
| 2GIT | 47QTCA21A000Y | Federal | |
| State of California Multiple Award Schedule (CMAS) | 3-16-70-1047B | State | California |
| State of Maryland Multi-Vendor COTS IDIQ | 06B02490021 | State | Maryland |
| State of New Mexico Multi-Vendor IDIQ | 50-00000-25-00077 | State | New Mexico |
VPN Can Hurt While Helping
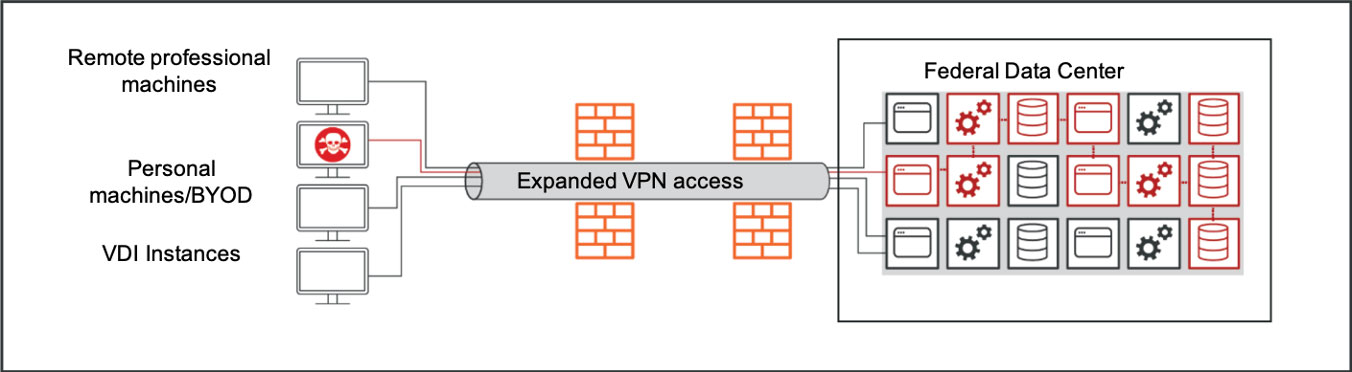
An infected work device that VPNs in from home can permit malware down the pipe and into the network, allowing viruses and malicious actors to traverse an organization and gain access to everything from legitimate workloads to high value assets. Read this blog post to learn more.
Maintain Your Cybersecurity Posture in Remote Work Environments With Illumio:
Adaptive User Segmentation
If you have a VDI infrastructure, Adaptive User Segmentation (AUS) takes advantage of Microsoft Active Directory (AD) User Groups to control access to computing resources in your organization. You can write rules with these groups to control outbound access on specific workloads based on the user's group membership. Learn more about AUS here.
Quickly Reduce the Attack Surface of Your Flat Network
If your network is flat, you need a quick and streamlined approach to identify, discover and ringfence your high-value assets (HVAs), so that you can reduce your attack surface during a transition to a remote work environment. Illumio's host-based micro-segmentation architecture allows you to accelerate your time-to-value while avoiding the cost, risk, complexity and lengthy deployments associated with software-defined networking (SDN)/networking and data center firewalls.
Extend Visibility and Control into Remote Machines
- Illumio's real-time application dependency map (Illumination) lets you visualize the authorized remote machines that have legitimate connections to data center applications.
- Create unmanaged workloads to whitelist the trusted IP addresses of machines that you want to allow into the data center and to connect to HVAs. To mitigate risks from IP-spoofing, AdminConnect uses PKI certificates to authenticate the identity of an authorized machine before it can connect to a data center application.
- The combination of unmanaged workloads with AdminConnect ensures only legitimate remote connections to your HVAs.