Flashpoint is the globally trusted leader in risk intelligence for organizations that demand the fastest, most comprehensive coverage of threatening activity on the internet. From bolstering cyber and physical security, to detecting fraud and insider threats, Flashpoint partners with customers across the private and public sectors to help them rapidly identify threats and mitigate their most critical security risks.
For more information, visit https://www.flashpoint-intel.com/.
Flashpoint Intelligence Platform grants access to our archive of finished intelligence reports, data from illicit online sources, compromised credentials from data breaches, and risk intelligence observables in a single, finished-intelligence experience. Key features include a universal search for all Flashpoint illicit community data, intuitive pivoting from reports into a sanitized copy of threat-actor conversations, and translated conversations, enabling native language content from illicit communities in English within the platform. Flashpoint’s datasets include:
- Finished Intelligence: Access to analytical reports produced by our intelligence analysts that cover illicit underground activity, including violent extremism, and physical threats.
- Forums: Access to signal-rich discussions from illicit threat-actor communities supplements and complements internal data with targeted data from highly curated sources.
- Risk Intelligence Observables (RIOs): A high-fidelity feed of cyber observables. RIOs integrate with security operations to enrich user data with additional context.
- Technical Indicators: Access to indicators of compromise (IOCs) and technical data across Flashpoint datasets.
- Paste Sites: Enables access to openly shared research, data leaks, and other plain text files frequently used by anonymous sources and threat actors to share malicious activity, providing a broader view into open web data.
- Card Shops: Users are provided credit card data including BIN numbers, country location, and expiration dates within these collections of stolen payment card data found in illicit high-end credit card shops.
- CVE: Access to the latest CVEs within Flashpoint collection, including access to MITRE and NVD data, as well as CVEs discussed by threat actors as observed by Flashpoint intelligence analysts and embedded technologies.
- Blogs: A view into online sources of news and information related to threat actors and collectives, allowing users to monitor activity in malicious communities comprehensively, as well as risks impacting the organization or brand.
- Account Shops: Customers can identify their organization's compromised accounts found for sale in illicit account shops, further stifling the risk of employee or customer login details being used in credential stuffing attacks.
- Marketplaces: Access to top-tier marketplaces, where threat actors buy and sell items such as stolen credentials and personally identifiable information (PII).
- Chat Services: Access to around-the-clock conversations within threat-actor channels to monitor and gain insights across threat-actor communities. Collections include Telegram, Discord, as well as Chinese-speaking threat actors.
- Message Boards: Access to these anonymous message boards, enabling users to monitor malicious content and discussions ranging from hacktivism to physical threats.
- Compromised Credentials: Allows users to monitor exposure of compromised credentials for their employee and customer email addresses to take action after breaches to mitigate risk of account takeover (ATO).
Public Sector organizations require reliable, actionable intelligence in support of their missions. Illicit online communities are a key and necessary source for critical intelligence in support of a variety of operations. Gaining access to information on cybercriminals, extremist groups, illicit marketplaces, money laundering, and risks directly affecting the agency is often difficult and dangerous to obtain. Furthermore, supporting the organization to build and grow a specific program to leverage this intelligence in support of these missions can be a challenging effort.
Flashpoint Professional Services offerings enable intelligence and investigations teams to support further analysis, and produce intelligence in support of their mission. Flashpoint’s services enable teams to augment their current operations, plan and build programs that map to specific intelligence requirements, and train teams to build the necessary skills to perform the duties to support their mission.
 Staff Augmentation
Staff Augmentation
OVERVIEW
Flashpoint helps public sector organizations reduce the challenges of overwhelmed or under-resourced security, intelligence, and investigative functions and can accelerate growth in both capabilities and efficiency for new or expanding teams. This service provides flexibility for organizations to ramp up to support investigations, meet demands, and mitigate risk while leveraging the experience and expertise of Flashpoint Professional Services to support needful growth within their organization.
FOCUS AREAS
- Cyber Threat Intelligence
- Physical Security
- Impact-Based Response
- Financial Crime
- Cyber Threats to the Agency
 Capabilities Building
Capabilities Building
Flashpoint Professional Services will assist the organization in either building a new program or in the enhancement of the current program, focusing on their direct needs and specific requirements. This service offering is customizable and driven based on the organizations’ needs and requirements. In support of building out capabilities, Flashpoint continues to support the organization by directly providing services, leveraging Flashpoint’s traditional products and services offerings.
 Training
Training
Flashpoint Professional Services offers specific training for departments and agencies seeking to build the necessary skills to enhance various areas of their security and intelligence programs. Targeted participants may include intelligence analysts, investigators, Security Operations Center (SOC) teams, Insider Threat Program (ITP) members, and Incident Response (IR) personnel, as well as supporting the awareness for an organization’s general workforce.
Use Case — Mission Support
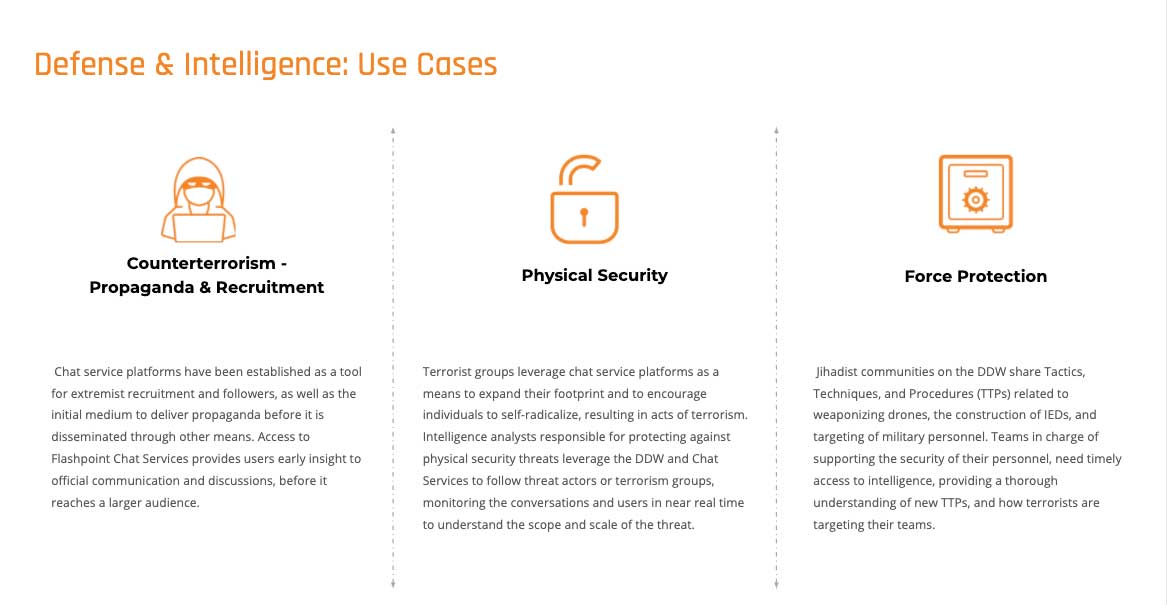
Tracking Terrorist Activity
Over the past several years, various extremist groups have used online platforms as a tool for extremist recruitment, the spreading of propaganda to encourage individuals to self-radicalize, and sharing tactics, techniques, and procedures (TTPs), resulting in acts of terrorism. Flashpoint’s support of public sector organizations through unique access to these illicit online communities, not only allows us to incorporate highly differentiated and signal-rich, unclassified data into our analysis, but also provide access to primary sources. This intelligence empowers organizations — from Law Enforcement, to Federal Civilian Agencies, to Defense and Intelligence — to make informed decisions in support of key mission objectives, potentially leading to the identification of those sharing and consuming terrorism content.
Our partners work with us to provide unmatched visibility into threats, empowering users with the context they need to make better decisions about risks posed by cybercrime, fraud, corporate and physical, and cyber threats.

Explore various blogs by Flashpoint, related to the public sector:
| Contract Name | Contract Number | Sector | State |
|---|---|---|---|
| CIO-CS | HHSN316201500012W | Federal | |
| National Cooperative Purchasing Alliance (NCPA) - Systems and Information Management Software | 01-164 | National | Texas |
| SEWP V | Group A: NNG15SC07B; Group D: NNG15SC98B | Federal | |
| TIPS | 210101 | State | Texas |
