Cloud Computing, Internet of Things, Technology
Ah, the good old days, when things were simple. When there were a known number of devices on any government network, and the federal IT pro had a complete understanding of how to secure those devices.
CAD General, Infrastructure, Technology
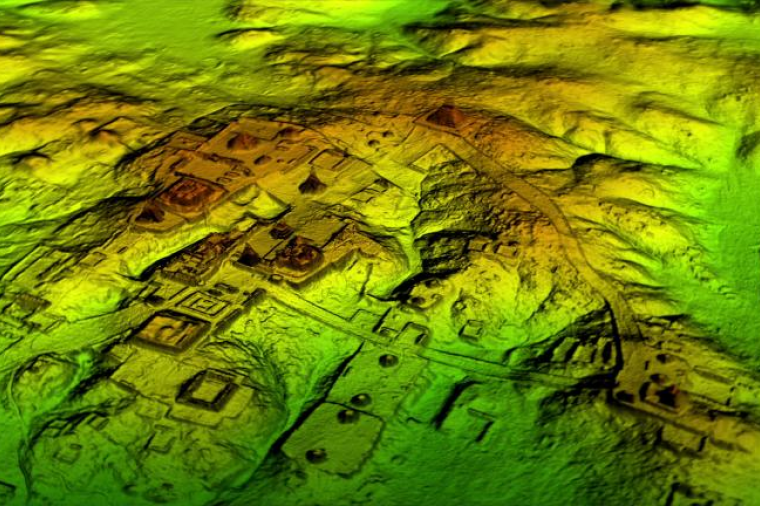
Archeological surveys in untouched areas are tricky at the best of times. Vegetation and trees must be disturbed, heavy equipment is brought in, and the results can still prove inconclusive or fruitless.
But thanks to laser technology, that’s all changing. LiDAR (aka Light Detection and Ranging technology) is helping archeologists champion scientific research without disturbing the natural habitat.
Cloud Computing
Just about every type of existing application is currently being migrated or considered for migration to a cloud infrastructure. While priorities vary from agency to agency based on mission priorities and/or application development and re-platform priorities – the pattern is clear. And, with the passing of the Modernizing Government Technology Act (MGLA) into law in December 2017, the funds to spur agency migration to the cloud are there.
Valerie Rider
Internet of Things
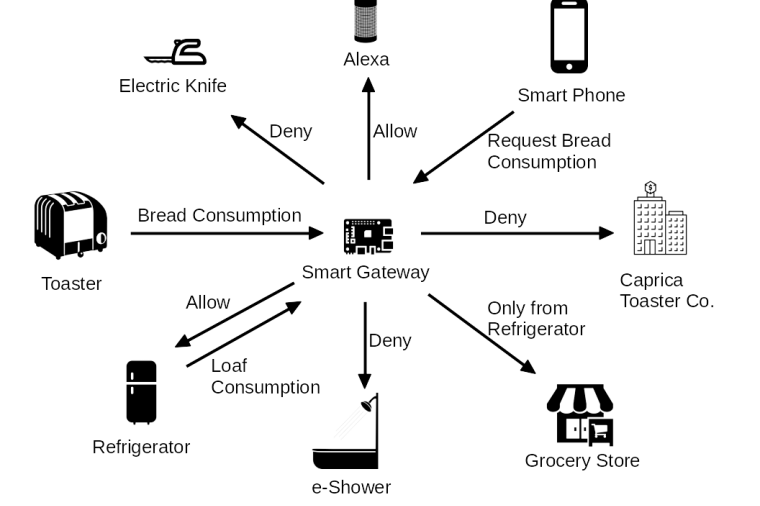
I believe that the Internet of Things (IoT) is a popular topic, in part, because its science-fiction becoming science-fact. IoT promises all of the conveniences of “The Jetsons” without having to push buttons, while threatening to produce the surveillance states of “1984” or “Minority Report”. Unfortunately, it most likely will give rise to the annoying doorways from Douglas Adam’s “Hitchhiker’s Guide to the Galaxy”, that have micro-transactional charges per use and in-app purchases that “allow” the door to open after 5pm. For our
CAD General, Technology
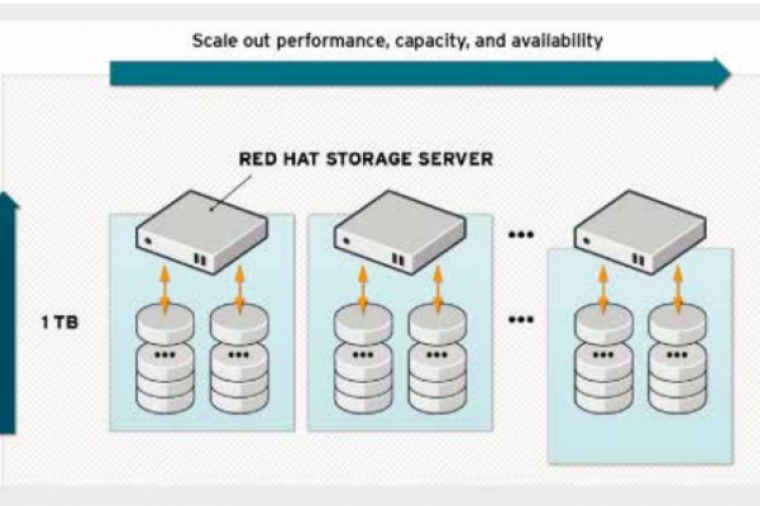
Traditionally, organizations world-wide have utilized Scale-up architecture when it comes to storage. What does this mean? Traditional scale-up architecture utilizes a dual-controller set-up, and adds storage drives as needed to increase storage capacity and performance. Run of storage, add another shelf. Seems pretty straight forward right? Run out of performance, not so straight forward...
Cybersecurity
How secure is your user access to AWS infrastructure and workloads? Security to protect every user’s access to apps, endpoints and infrastructure when moving to the cloud is a hot topic. AWS’ shared responsibility model means that security and compliance is just that, shared between AWS and the customer.