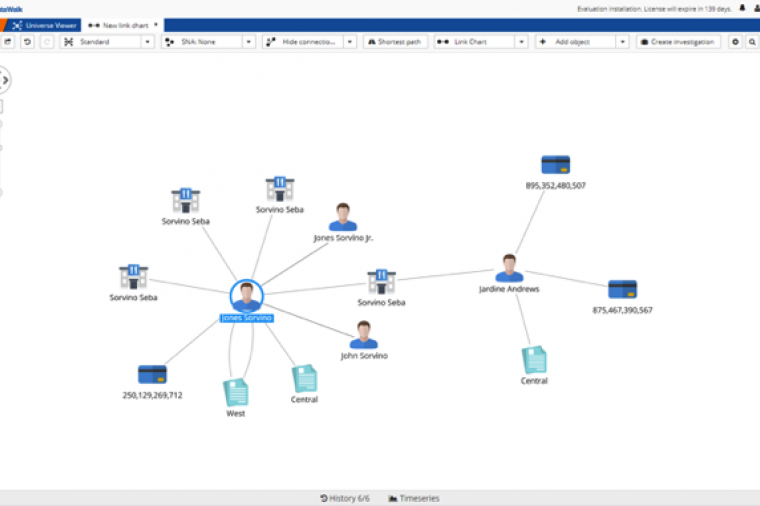
Big Data & Analytics
At DLT, July is Big Data Month, where we will be highlighting all things big data in the public sector. To kick off Big Data Month, we sat down with DLT Chief Data Scientist Sherry Bennett to get her insights into what is going on the world of public sector data and analytics:
INTERVIEWER: So Sherry, what's your story and what led you to DLT?
Data and Analytics, Infrastructure
Government networks are some of the largest in the world. Ensuring these mission-critical infrastructures are optimized for automation and performance—particularly in today’s increasingly complex hybrid IT environments—is quite a tall order.
How do federal IT pros ensure the high availability required? How do they connect faults to performance, and make direct connections between networks, systems, and applications within large, hybrid environments?
Digital Design
Rich3D, GovDesignHub explain how they delivered complex helicopter and military vehicle 3D virtual training via a ubiquitous tool – an Adobe Acrobat document.
The U.S. Marine Corps and the U.S. Navy need highly interactive 3D tools to deliver complex animated virtual training and simulation environments for helicopter pilots, crane operators and other professionals. And government contractor Rich3D uses a variety of 3D design tools to develop and deploy the interactive training environments they need.
Cloud Computing, Cybersecurity
Government agencies are moving to the cloud. It’s been a recurring message for a number of years, but in 2018 new statistics from Gartner give us concrete data on cloud spend: local governments spend 20.6% of their IT budget on cloud, while national governments spend 22%.
Digital Design
For government organizations and municipalities, ensuring everyone is on the same page in terms of core competencies is an essential prerequisite to the success of any digital design or engineering project. With the pressure to do more with less, knowledge gaps can stymie team productivity, lower your return on investment in software tools, and make everyone’s lives a lot more difficult.
Cloud Computing, Data
Federal government agencies as well as states and cities are rich repositories of data – data on everything from health to public safety, education to the environment. But those same organizations have moved beyond being isolated data storehouses. Data is no longer locked away on devices and storage drives, hidden behind firewalls. Instead, it’s becoming distributed (cloud and on-premises), dynamic (the velocity of data from sensors, citizen attributes, etc. is constantly fluctuating) and diverse (structured, unstructured, and streaming).
dana.suarez