Vulnerability in SLED: How the Threat Landscape is Changing to Target Education, Small Municipalities

The Cybersecurity and Infrastructure Security Agency (CISA) has seen increased malicious activity with ransomware attacks against K 12 educational institutions. Malicious cyber actors target school computer systems, slowing access, and rendering the systems inaccessible to essential functions, including remote learning. In some instances, ransomware actors stole and threatened to leak confidential student data unless institutions paid a ransom.
Ransomware attacks on US government organizations cost $18.9bn in 2020.
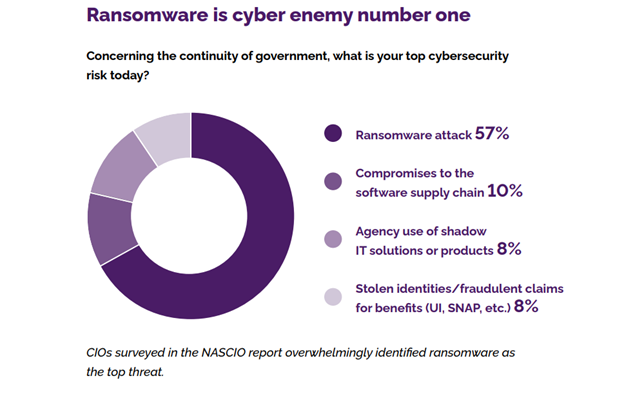
Even prior to the pandemic, state and local governments were frequent targets of successful ransomware attacks. Although many governments paid the ransom, some resisted, incurring significant data recovery costs in doing so. Even more costly than these payouts, downtime is the cause of most ransomware losses. Comparitech estimates that government agencies lost 5,642 days to ransomware attacks. With every minute of downtime costing an estimated $8,662, the overall cost of the attacks could be $18.88 billion.[1]
The past two years of experience have reshaped our priorities, identities, and worldview, drawing a bright line between what’s important — health, family, time, and purpose — and what’s not. People are now more likely to prioritize their health and well-being over work than before the pandemic. As a result, employees’ “worth it” equation of what people want from work and what they’re willing to give in return has changed. In Microsoft study, 47% of respondents say they are more likely to put family and personal life over work than they were before the pandemic. In addition, 53%—particularly parents (55%) and women (56%)—say they’re more likely to prioritize their health and wellbeing over work than before.
Despite the digital overload, people are doing flexible work independently, taking control of their time and reshaping the workday. That natural forefront of implementing new technology usage by organizations and end users shines our light on our priority as end users and data moving forward due to the pandemic. “Covid has not been all doom and gloom for me. It forced me to dig deep and reevaluate what is important.” Self-employed education professional, Canada.
Since pandemic, uninvited users have disrupted live-conferenced classroom settings by verbally harassing students, displaying pornography and violent images, and doxing meeting attendees.
Top Common threats in k-12 education and small municipalities:
- MALICIOUS CYBER ACTOR Person, group, or entity that creates all or part of an incident with the aim to impact an individual’s or organization’s security
- DOMAIN SPOOFING The act of registering web domains like legitimate websites to trick individuals who mistype URLs or click on similar looking URLs
- DOXING The act of compiling or publishing personal information about an individual on the internet, typically with malicious intent
- END OF LIFE SOFTWARE Out-of-date software and equipment that no longer receives patches, security updates, technical support, or bug fixes, making the user vulnerable to attacks.
- PHISHING/DECEPTIVE E-MAILS The fraudulent attempt to obtain sensitive information or data, such as usernames, passwords, and credit card or bank account details, by disguising oneself as a trustworthy entity in an electronic communication
SLED entities are burdened by an onslaught of security threats such as ransomware attacks. Shoring up their defenses and dedicating funding to cybersecurity will take priority in the next few years. Local governments, particularly smaller ones, can be easy targets since they typically have fewer resources and staff with cybersecurity expertise.
Government officials have faced enormous difficulty recruiting and retaining strong cybersecurity talent in the workforce, therefore struggling to build a strong team of security professionals to safeguard state networks and carry out their cybersecurity mission. Most state CIOs have stated that their top cybersecurity challenges and priority gaps revolve around a lack of staffing, funding, resources, and stakeholder buy-in. With the right people, protecting public sector networks from threats and attacks becomes easier.
Furthermore, the types of security attacks have increased in complexity and threat level. We no longer see “basement-level hackers” but those who treat this as a full-time job, such as nation-state actors, espionage, phishing, social engineering, etc. The biggest challenge in this regard is to identify the source of the attacks. They often come directly from the US and sometimes within the attack state. Solutions such as vulnerability analysis, patching, and remediation can help. Many government entities also emphasize the importance of a zero-trust architecture and user awareness training. For instance, if you can train 1500 people on staff, you now have 1500 individual users analyzing threats instead of two.
Following suit with the federal government, the whole-of-state approach to cybersecurity will continue to serve as a foundational model for SLED entities. State cybersecurity operations are working to strengthen collaborations with local governments and public universities as this model continues to garner attraction. However, cooperation and relationships amongst these entities remain limited, with more than 50% of state CISOs reporting “limited collaboration” with local governments, state universities, community colleges, and K-12 districts. Another example: the CIO of Iowa’s top concern around Iowa’s whole-of-state program is building awareness of his state’s services among smaller governments, which includes cybersecurity and general IT services.
Many states now have dedicated line items for cybersecurity, with some spending more than 10% of their technology budgets on security (close to that of federal agencies). Several federal initiatives and funding. As modernization and digitization efforts continue to define the current landscape, cybersecurity risks also continue to grow, putting our country’s infrastructure at high risk.
Research has found that it’s not that SLED is the most popular target, but that their systems are often the most vulnerable. Tight budget and short staffing mean defenses are unsophisticated, and systems are left unpatched with security updates, Another NASCIO survey found budgeting, staffing, and legacy infrastructure to be the main cybersecurity obstacles facing state and local agencies.

Lack of funds and staff, coupled with legacy infrastructure, make state and local agencies vulnerable.
Specific cyber prevention technology measures and solutions will continue to gain attention over the next few years, including how we are evaluating, web isolation, threats modeling with a broad landscape, robust fraud prevention, securing a reliable backup system, training staff, and testing for vulnerabilities, multi-factor authentication (including remote work), and a zero-trust architecture model.
Resources:
https://www.comparitech.com/blog/information-security/government-ransomware-attacks/
https://www.microsoft.com/en-us/worklab/work-trend-index/great-expectations-making-hybrid-work-work
https://home.treasury.gov/system/files/136/FRF-Interim-Final-Rule.pdf
https://www.threatadvice.com/sled