From the CISO: Why Columbia University Medical Center Made the Move to Cloud-Native Cybersecurity

More and more organizations are making the move to cloud-based security solutions. Today, 33 percent of organizations are planning to adopt one or more security-as-a-service (SECaaS) solutions. The efficiency with which endpoint security solutions can provide protection, particularly when delivered as-a-service, is a key strategic consideration for many organizations – perhaps none more so than America’s network of medical schools and teaching hospitals.
One such institution is Columbia University Irving Medical Center (CUMC) located in New York, NY. In a recent webinar, hosted by DLT Solutions and CrowdStrike, CUMC’s Chief Information Security Officer (CISO), Brian Smith-Sweeney discussed the crucial security issues impacting today’s university organizations and how choosing the best cloud-based cybersecurity solution can be challenging.
Supporting Intersecting Yet Disparate Missions
To frame the discussion, Brian first defined the unique, yet intersecting, missions that technologists at CUMC and any medical academic center must serve: medical education, research, and patient care.
“There is almost no sector that you can do more good right now as a security professional than in healthcare and in academic medicine,” said Brian. Yet, while serving each of these discreet missions is rewarding, it’s also a big challenge. Disparate communities of people – educators, students, and researchers – puts unique pressures on the security professionals at CUMC.
Educators and students, for example, are digital natives. They expect easy access to course material, management tools, and other resources – anywhere, at any time, and from any device.
Researchers have similar needs, but also value leading-edge technology (often developed in-house) that can be rapidly deployed while adhering to compliance mandates. This community is pushing the boundaries of technology, medicine, and research, which, in turn, pushes the boundaries of any security program.
Patient care has unique demands of its own. IT systems must be stable and highly-available. They are also highly interconnected and have long refresh cycles, that require constant patching (think MRI machines and scanners).
Brian’s remit also includes administrative functions at CUMC – where technology is often an afterthought, but still needs to work 24x7.
Facing these Challenges in the Cloud
Faced with competing yet overlapping missions and communities, a key requirement is systems that are scalable and cost-effective. So how does the cloud help CUMC’s security operations?
Security aside, the cloud delivers many benefits for IT and business teams alike. The notion of self-service enables quick deployment of services (without the involvement of IT), while broad network access provides access to data and application from anywhere in the world. Resource pooling and rapid elasticity support spikes in workload. And, because the cloud is a measured service you pay only for what you use, as you go.
Each of these cloud capabilities also maps to the security function. Consider the following:
• On-demand self-service – Departments at academic medical centers often need to rapidly fire-up a service, which means the security operations center (SOC) must be ready to quickly scale-up a security solution. The cloud makes this easy. You simply call your provider, scale up the agreement, or turn on new features and secure the new system, often the same day. This all happens in a way that is seamless and transparent to the end user. “It’s a small technology thing, but it has a big impact on the way the organization might perceive the security team,” said Brian. “We’re doing this without getting in the way of what researchers are trying to accomplish. It’s a real service to the community.”
• Broad network access – Missions and student and educators expect access from any device, anywhere. And, while cloud has destroyed the network perimeter, it’s also a remedy for the security risk this poses. Using tools like CrowdStrike, if someone works from home or a researcher happens to be visiting <hostile country> on Friday, the security team can quickly and easily expand security outside the four walls of the organization.
• Rapid elasticity and resource pooling – You can’t beat cloud-based tools for scaling up quickly, and security tools are no exception. But not only do they scale quickly, they require little intervention from IT. Thanks to the self-service capability of the cloud they “just work”, said Brian. “We don’t have to deny scale-out because our security tools can’t keep up.”
• Measured service – “I love subscription models,” said Brian. “I was never a fan of the old way of financing… A measured service provides an opportunity and incentive to review whether we are getting value from our investment. We can now say what it costs to deploy this security function, this is how many incidents we stopped, and we can break down cist by the things we prevented on a very granular level – that’s fantastic and is a great conversation to have with leadership.”
Phishing Interrupted
An interesting comparison of legacy on-premise security tools versus cloud tools also came out of the discussion. In the past, when faced with a phishing attack, Brian described a SOC that would have been scrambling to answer a series of questions that just go and on:
• Do we know who else got this? Do we control the machine?
• Should we send an email out to everyone?
• Who fell for it? Do we reset passwords?
• What about home users?
• What about password re-use?
• How do we…?
Using an example of a phishing email sent to executives from known CUMC executives and containing a link to a seemingly trusted internal resource, Brian explained how, using CrowdStrike, his team can now identify threats rapidly, get an end-to-end picture of what happened, and respond in real-time:
“We know who got the phishing email, who clicked on the link, why it might have been allowed through. We also know which workstations are affected, what filesystem was modified, what network activity was observed, and what DNS queries were made. Within seconds we can figure out what happened – end-to-end. We can then quarantine the software using a Content Disarm and Reconstruction (CDR) tool. CrowdStrike does this very well and I’m very, very happy we have it.”
The Key to the Cloud’s Success – Flexibility
When asked to sum up the benefits of cloud-based security, Brian had this to say: “Cloud gives us flexibility. Flexibility in how we provide services and provide security services to everyone on campus. CrowdStrike gives us that ability.”
Brian continued: “Using security tools that have flexibility built-in, lets you scale-out, lets you serve your community’s needs, lets you accomplish your security goals across a wide variety of needs – without getting too caught up in trying to right-size or one-size your solution for everybody. We like that a lot.”
This flexibility is key for organizations like CUMC characterized by distributed IT teams and distributed governance. “The process is formalized and works well, but these groups expect to have control and visibility into their own infrastructure,” said Brian.
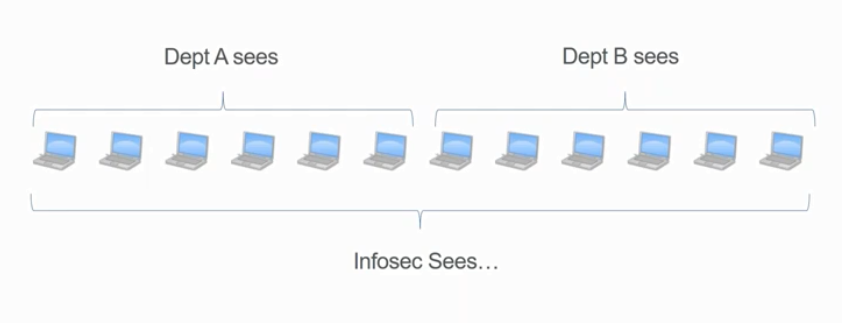
“A tool like CrowdStrike provides a ton of visibility. We’ve sliced up our systems into departments. Each has visibility into what they need to meet their IT needs and privileges, while InfoSec can see everything. It’s a pretty huge win and gives our engineers the flexibility to manage the system, while our responders use and improve the system.”
Considerations for Migrating to a Cloud Security Infrastructure
Brian also offered some useful pointers about considerations when moving from on-premise to cloud security tools.
• Have a conversation about what you want to be good at – Consider the talent you want to maintain internally versus what the cloud solution provides picks up for you. Ask yourself what you want to be best at, whether it’s email security, endpoint security, and so on.
• Due your due diligence – While Brian is adamant that a cloud infrastructure is the right way to go for web security tools, each organization is unique. “My tools aren’t specifically the tools you want, I love our CrowdStrike implementation, I love our security gateways – but go through the process of investigating the security tools you want to use.”
• Accept that rapid elasticity and resource pooling is finite – This often comes as a surprise to anyone consuming SaaS, particularly security services. “We definitely had areas where any of our providers did not behave in as performant a manner as we had hoped – and you can understand why,” said Brian. “When you’re talking to cloud security providers they’re always kind of say ‘don’t worry about the resources, it’s in the cloud, we can scale infinitely’ and while theoretically, that’s true, in practice you’re probably paying a static rate for your SaaS or maybe you’re paying by license of the number of people – you’re not paying by compute or bandwidth. But somebody is paying for those things, and it’s usually your provider.”
The advice here is: be comfortable knowing that troubleshooting involves a call to a help desk or a negotiation with a provider and there may not be an immediate fix.
Learn More
To learn more about Brian’s experiences and recommendations for migrating from on-premise security to cloud tools like CrowdStrike, watch the on-demand webinar: Transforming Medical Universities with Cloud-Based Cybersecurity Tools.
About Brian Smith-Sweeney
Brian Smith-Sweeney was appointed Chief Information Security Officer at Columbia University Medical Center in 2015. He feels incredibly fortunate to have been able to turn something he loves into a 20-year career. Brian enjoys speaking publicly, especially about infosec, and is passionate about data-driven decision making, FUD busting, and building communities.
Brian works with an amazing, diverse, and dedicated team of security professionals at CUMC. With their help, he sets the direction and provides overall security leadership for the Medical Center with a focus on threat management and HIPAA compliance. Prior to joining the Medical Center Brian held a variety of roles at New York University including Assistant Director of Global Security Operations, heading up a program that spanned twelve countries, and before that he worked as an IT consultant and security professionals in both the public and private sector.
Brian has been an active member of the higher education security community and has worked on the Internet2 SALSA-CSI2 working group, the REN-ISAC Transitional Board, and the REN-ISAC Microsoft Analysis Team which he chaired. He has also been a regular contributor to the Educause Security Professionals Conference and chaired the 2015 program committee.
But those are just his hobbies – his real job is as a husband, and a father and personal chef to three awesome kids.

















































