Are Your Endpoints a Risk? Take Control, Detect Risks, Automate Your Response
Getting to know the “enemy with no face” is critical to winning the cyber war. In fact, it’s the tagline from the U.S. Army’s latest cyber warrior recruitment ad. Yet, one of the biggest challenges to doing so is that most organizations have zero visibility into a significant percentage of the endpoints on their network. That’s because they are either not managed (BYOD, guest, and IoT), have disabled or broken agents, or aren’t detected by periodic scans.
Not only does this make it impossible to know who and what is on your network, it exposes you to attacks that exploit well-known vulnerabilities and security gaps on endpoints connected to your network.
It doesn’t have to be that way. DLT partner, ForeScout Technologies, now helps agencies ensure device security with an ePO Integration Module that allows ForeScout CounterACT® to integrate with McAfee ePO. With this integration, you get real-time visibility and control over managed and personal devices and automated network access control.
ForeScout CounterACT is a network security appliance that provides IT organizations with the unique ability to see devices, including non-traditional devices, the instant they connect to the network.
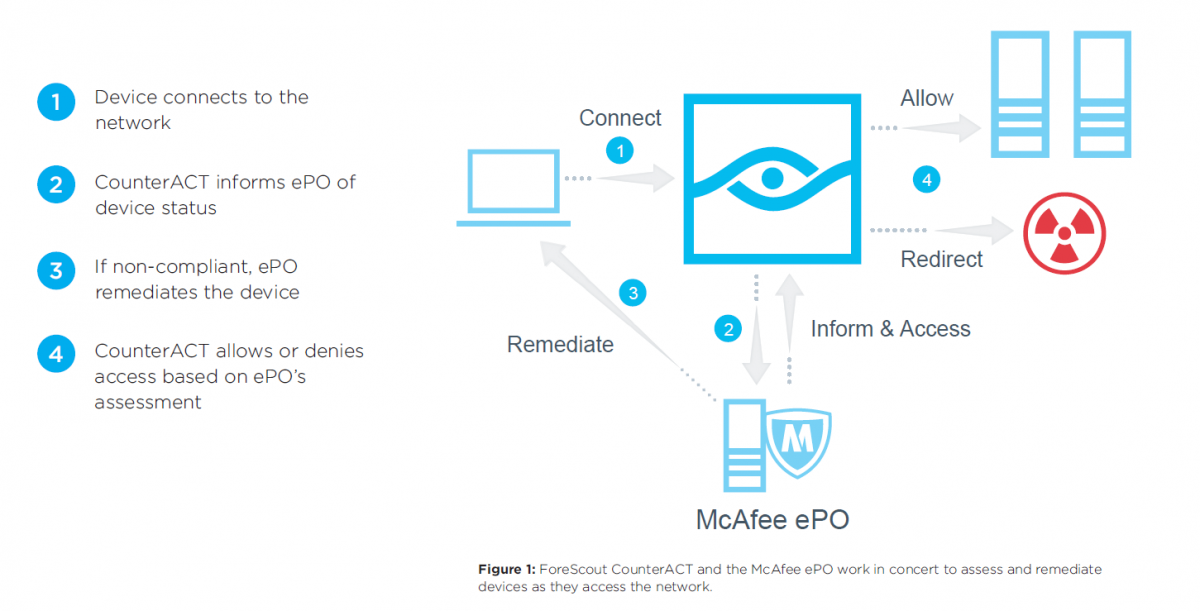
If the connecting device is an agency device and has a McAfee agent installed, ePO tells CounterACT what it knows about the endpoint compliance status of the device. If the device does not have a McAfee agent, CounterACT will inspect the device to determine its compliance status. If the device is compliant, and the user is authorized, CounterACT allows the device to access the appropriate network resources, according to your policy.
If a McAfee agent is missing or broken, CounterACT alerts ePO to install or repair the agent. If this is unsuccessful, CounterACT will either attempt to install the McAfee agent directly, or, it will capture the endpoint’s browser and will send the user to a self-remediation page. CounterACT also notifies the ePO Rogue System Detection about unauthorized or non-compliant devices.
Once admitted to the network, if ePO determines that the endpoint has become non-compliant, ePO can be configured to tag the system and immediately report its non-compliance to CounterACT, which can isolate the endpoint until remediation has been performed. CounterACT also continually monitors the endpoint to determine if its behavior becomes threatening. For example, CounterACT may isolate the endpoint, disable the USB port, or kill an unauthorized application.
Want to know more? Join DLT, McAfee and ForeScout for a 30-minute webinar on Friday, December 15, 2017 at 2.00 PM EST. You’ll learn about how you can gain real-time threat insight and rapidly mitigate risks from unmanaged and BYOD endpoints. Register here.

















































