Time is Running out for Government Contractors to Meet Key Cybersecurity Compliance Deadline

Time is running out for federal contractors to comply with the Federal Controlled Unclassified Information (CUI) Program.
What does the CUI Program mean to contractors?
As of December 31, 2017, all federal contracts will require that businesses contracting with the federal government must comply with the Federal CUI rule (32 CFR Part 2002) which strives to eliminate ad-hoc policies and markings that agencies and departments apply to unclassified information that requires safeguarding or dissemination controls.
As stated in Executive Order 13556, “This inefficient, confusing patchwork has resulted in inconsistent marking and safeguarding of documents, led to unclear or unnecessarily restrictive dissemination policies, and created impediments to authorized information sharing.”
Instead, the CUI Program establishes a uniform, shared, and transparent system for protecting CUI. These security requirements are defined in NIST Special Publication 800-171, which applies to CUI in non-federal information systems and organizations.
How do we comply?
Compliance with the CUI Program isn’t just about protecting sensitive government information, it’s about making industry accountable for that information that they work with every day. As cybersecurity threats increase, the federal contracting community is being asked to do business in an even more regulated environment. What are your options for compliance?
There are many tools and technologies that can help with compliance. TITUS, for example, a new DLT partner offers a commercial off-the-shelf solution that enables organizations to comply with CUI with minimal impact to internal IT and software development resources. TITUS removes the burden of compliance by automating the tasks of identifying CUI in email, documents, and files and applying CUI-compliant markings and distribution limitations. These markings raise CUI awareness and encourage information sharing and proper handling of sensitive information.
The solution also warns users when they are violating policy, such as sending CUI to a recipient who is not authorized to receive it. It also enhances the ability of other security solutions to protect CUI, including encryption, DLP, network guards, and archiving solutions.
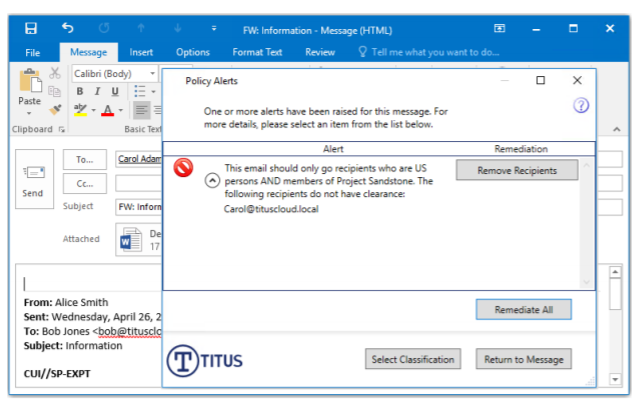
TITUS prevents inadvertent disclosure by checking recipient clearance. Read more about the ways in which federal contractors and agencies who need to identify and protect CUI can use TITUS.

















































