The Threat Landscape – 2016 in Review, and What’s Ahead for 2017

Got breach fatigue yet? Yes, it’s been another bad year for computer security. 2016 saw the announcement of the biggest breach ever – the Myspace hack. But, that was quickly eclipsed by the September Yahoo data breach which resulted in the exfiltration of extensive account information, included passwords, from 500 million users. Not to be outdone by itself, in December, Yahoo announced a second breach – this time implicating one billion users!
But while we often focus on the headline-makers, several significant security events and malware threats appeared throughout the year and will go on to play a big part in the emerging threat landscape of 2017.
DLT partner, Symantec has been tracking these developments and shared its “year in review” in a recent webinar hosted by Kevin Haley, Director of Security Technology and Response at Symantec. You can watch it on-demand here. By way of a quick recap, here are some of the highlights, plus a look ahead to the security threats we’ll be talking about in 2017.
The 2016 Threat Landscape Reflected a Shift in Motives
Breaches aside, Symantec informs us that one of the big observations to make about the threat landscape in 2016 is the shift in motives of cyber attacks.
In 2016, not only did threat actors start going after the big money, conducting targeted and sophisticated attacks on financial institutions, targeted ransomware also rose where attackers negotiate with victims on a ransom amount. The average ransom per machine is now $679, up from $294 in 2015.
Below is a chart, courtesy of Symantec, that shows the progression of motives and tactics in the last three years:
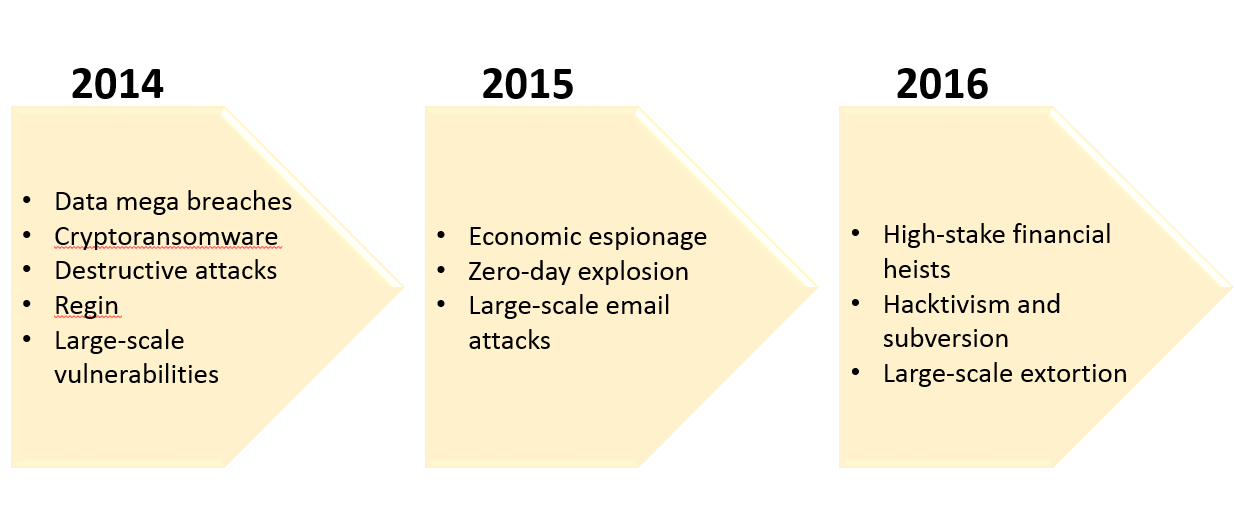
Other developments included:
• Upswing in Politically Motivated Hacks – Subversion and hacktivism experienced a notable upswing in 2016 and is likely to continue to rise. Take, for example, the DNC email hacks. The attacks were carried out by a Russian group known as the Bears. The group was already associated with attacks against high-profile individuals and organizations in government and international policy. The DNC Gmail attacks, which utilized targeted phishing were politically motivated, which sets them apart from the more conventional economic espionage attacks of recent years.
• Denial of Service (DDOS) Attacks Using IoT Botnets Emerged – Another form of subversive or hacktivist attack that became more prevalent in 2016 was the use of IoT devices as a vehicle for DDOS attacks. Poorly secured, Symantec notes that these devices are often attacked within two minutes of coming online. Lacking any form of patching ability or even inherent security software built-in, upping the protection of IoT devices is all but impossible. The poster child case in 2016 was the Mirai botnet composed of over 100,000 poorly protected IoT devices. The initial target was a French security blogger, then the attack moved onto a French ISP provider, until it hit DNS provider Dyn, which services several well-known sites, and shook the Internet – clearly demonstrating how cloud-services are susceptible to attack. Check out this blog from Symantec for tips on protecting your IoT devices from DDOS attacks.
• Zero-Days Declined – But That’s Not Necessarily a Good Thing – None of the high-profile breaches from the past 24-months examined by the NSA involved zero-day attacks. A zero-day vulnerability is an unknown vulnerability that hackers can exploit to adversely impact networks, programs, and data. This doesn’t mean that zero-day is obsolete, warns Symantec. It simply means that zero-day isn’t employed as much since the security posture and hygiene at many organizations is so poor that such sophisticated tools aren’t needed to penetrate the network.
• It Got Harder to Detect Intruders – An increase of PowerShell use by cybercriminals and state actors is making it much harder to detect an intruder once they’ve broken in.
• SpearPhishing Tactics Changed – Instead of using attachments, spearphishing has shifted to utilizing email links in targeted attacks, such as the one against the DNC.
What Will 2017 Bring?
Symantec anticipates the following trends for the year ahead:
• Subversion Will Be the New Espionage – While economic espionage attacks against U.S. targets will continue to decline, organizations will increasingly be attacked for subversive purposes. Instead of just stealing data, data may be open to manipulation or an environment might be changed so that its integrity is brought into question.
• Data will Become Increasingly Vulnerable – In addition to manipulating data for subversive purposes ransomware will start to target cloud data.
• Cybercriminals will Continue to Seek the Big Win – An increasing professionalization of cybercrime means that larger financial attacks will become the norm. Centralized systems and vulnerable software will also expose organizations to repeated attacks.
• Attackers will Continue to Hide in Plain Sight – Because it’s no longer necessary for attackers to develop custom tools and exploit zero-days, attackers will increasingly use generally available tools and techniques.
• Analytics will Become the New Security Weapon – Watching behaviors and incidents of compromise around hacker tools, will become more important than just scanning for malicious files.
Watch or download the full on-demand webinar here.

















































