On Thursday, November 17, Google and DLT Solutions are hosting a live technology seminar in Denver, Colorado. The Tech Day will be held at the Sheraton Denver West Hotel in Lakewood, CO.
Government agencies around the country are rapidly adopting Google's enterprise solutions to manage information & promote teamwork, while lowering their IT costs. Learn from Google product experts how these modern technology solutions allow you to meet the current challenges of your agency. You will see, in a briefing and in demonstration, today's art of the possible and a compelling vision for the future!
Google product experts will present on specific products, including Google Search Appliance, Google Geospatial, Google Apps, and Google Chromebooks. These experts will show how these modern technology solutions allow you to meet the current challenges of your agency. Andy Paratore, Chief Information Officer for Larimer County at Department of Employment & Training, will also be presenting about Larimer County’s use of Google Apps.
Discover how Google enterprise solutions can bring value to your agency.
- Bring the power of Google search to your enterprise data – behind the firewall! Even classified information can be searched, with security needs enforced.
- Promote better collaboration among employees with web-based email, calendar and documents that are designed for teams and accessible anywhere employees can access the Internet.
- With Google mapping tools, develop and visualize a common operating picture, easily deployable in networked, remote and mobile environments.
Related Blog Posts
Cybersecurity, Market Intelligence, News, Technology
table, th, td {
border: 1px solid #c9edfa;
padding: 5px;
}
The National Defense Authorization Act (NDAA) is passed annually to define the Department of Defense’s priorities and guide how funds are allocated. While it doesn’t directly appropriate money, it shapes the direction of defense spending and sets the framework for future contracts. This makes it a key indicator of where IT investments and opportunities will emerge.
Toan Le
Cybersecurity, Federal Government, Market Intelligence, News, Technology
In August 2025, President Trump signed an executive order titled “Improving Our Nation Through Better Design,” establishing the new “America by Design” initiative. The order aims to enhance both the digital and physical experiences of government services and facilities, signaling a major modernization effort focused on design, technology and user experience.
Nikki Hamlin
AI, Federal Government, IT Perspective, Market Intelligence, News, State & Local Government, Technology
The One Big Beautiful Bill Act (OBBA), enacted on July 4, 2025, is a significant piece of legislation outlining President Trump's executive agenda and guiding future U.S. tax and spending policies.
Yvonne Maffia
Federal Government, Market Intelligence, News, Technology
We’re still in the first quarter of the fiscal year and headed toward the holiday season. Historically, that predicates a slower pace across the federal sector, but not this year. This year, artificial intelligence (AI) is having a moment, and nearly everyone across the public sector, including the White House and The Office of Management and Budget (OMB), has something to say about it.
Susanna Patten
Cybersecurity, Federal Government, Market Intelligence, News
Federal Pain Points and IT Requirements
The latest Federal Information Technology Acquisition Reform Act (FITARA) Scorecard, released in December 2021, highlights how federal agencies are faring across several areas related to IT modernization. The full breakdown from the scorecard is available here. These scorecards are useful to identify where government agencies are struggling and where they are doing well. Consequently, technology vendors and channel partners can use them as a guide for identifying what solutions their customers need.
Dawit Blackwell
News
DLT's Josh Tehan has experienced every parent’s worst nightmare – being told your child has cancer. His son, Ethan, who is now cancer-free, was diagnosed with acute lymphoblastic leukemia (ALL) at the age of 3 and underwent three years of chemotherapy.
Now that Ethan is living the life of a typical, healthy 15-year-old, his dad wants to help other children and parents going through blood cancer treatment by raising money for the Leukemia and Lymphoma Society (LLS).
Brandon Norris
News
“Equality is not a women's issue, it's a business issue.
Gender equality is essential for economies and communities to thrive.”
Today, we at DLT are joining millions across the globe in observing International Women’s Day (IWD): a day to celebrate the social, economic, cultural and political achievements of women, and is a notable call to action to accelerate gender equality.
Isabella Jacobovitz
Uncategorized
Article originally posted on GovDesignHub here.
Autodesk University (AU) returns to Las Vegas from November 19-21 – and we have some good news. In addition to discounted conference passes now available on GSA Schedule, Autodesk Certification exams are back at AU 2019!
Caron Beesley
Uncategorized
By Mav Turner, VP, Product Management, SolarWinds
For federal IT pros, moving to a cloud environment is a “when” rather than an “if” proposition. From the government’s recently released Report on IT Modernization, calling for agencies to identify solutions to current barriers regarding agency cloud adoption, to the White House’s draft release of a new “Cloud Smart” policy, which updates the “Cloud First” policy introduced in 2010; cloud migration continues to be a priority.
DLT Solutions
Federal Fiscal Year End, Uncategorized
The old business adage runs, “Nothing happens until somebody sells something.” To which you might add this corollary: nothing good happens in the absence of strong requirements.
Brian Strosser
IT Perspective, Uncategorized
The latest data on the progress of federal government agencies’ implementation of the Federal Information Technology Acquisition Reform Act (FITARA) was released on June 26 by the House Oversight and Reform Committee as Scorecard 8.0.
Melissa Perez
Cloud Computing, Uncategorized
Key takeaways show how public sector customers are achieving more with cloud.
As cloud continues to transform the public sector, cloud has had its own metamorphosis: from a trendy buzz word to a catalyst for meaningful change, innovation, and more. Last month, AWS hosted its 10th annual AWS Public Sector Summit. The conference brought together more than 17,000 attendees for 2+ days of insights, sessions, and networking, and explored how cloud is fueling the public sector for a limitless future.
Recap
Isabella Jacobovitz
Uncategorized
Many states' fiscal years are quickly coming to an end, and at DLT we’re committed to making the job of the procurement officer as easy as possible as they scramble to make smart and responsible purchasing decisions with remaining taxpayer dollars. Part of this process is raising awareness of what’s new in our extensive portfolio of IT solutions including big data and analysis, cloud, cybersecurity, application lifecycle, digital design, IT consolidation and management, and more.
Brian Strosser
Uncategorized
Earlier this year DLT announced they were selected as the “Master Government Aggregator”
DLT Solutions
Business Applications, Uncategorized
Not all Ivy League schools have massive endowments and bank accounts. Some have to get more creative when looking to build new facilities on a budget – or simply embrace innovative new approaches to design and construction.
DLT Solutions
Business Applications, Uncategorized
It’s that time of year again! Spring is here and Autodesk has commenced its steady roll-out of 2020 software releases.
First off is AutoCAD 2020. Released in late March 2019, AutoCAD 2020 includes interesting and exciting new features. With a subscription to AutoCAD 2020, you’ll get industry-specific toolsets; improved workflows across all your devices – web, mobile, and desktop; and new integrations with cloud storage vendors.
Here’s a round-up of what’s new.
Kirk Fisher
Digital Design, Uncategorized
When we launched GovDesignHub in the spring of 2018, we had one goal in mind – to address the lack of resources, discussion, and analysis available online for those who practice in government digital design ecosystem.
Today, we’re proud to be the only website that showcases government design projects and the technology used to support them and deliver content to help public sector organizations accomplish their missions.
In the words of one of our top contributors, Lynn Allen, of Autodesk fame:
Holly Chapman
Federal Fiscal Year End, Uncategorized
Congress first enacted federal appropriations law in 1809. It’s kept lawyers, contractors, and judges busy ever since. A question arising in many sellers’ minds at this time of year is, what money is available for contracts in more than one fiscal year?
Tom Temin
Digital Design, Uncategorized
New York City Department of Design and Construction (NYC DDC) handles some of the most exciting and dynamic architectural and infrastructure challenges in the world.
Grace_Bergen
Cybersecurity, IT Perspective, News, Technology
Shortly after the federal government suffered it’s largest and costliest data breach ever at the Office of Personnel Management (OPM), a post-mortem analysis found that the breach was entirely preventable, and the exfiltration of security clearance files of government employees and contractors could have been prevented through the implementation of two-factor authentication for remote log-ons.
BradleyGernat
Digital Design, IT Perspective, News, Technology, Tips and How-Tos, Uncategorized
The CAD and digital design sector is vast and growing at breakneck speed. It’s expected to reach $11.21 billion by 2023.
Many end-use industries such as automotive, aerospace, entertainment, industrial machinery, civil and construction, electrical and electronics, pharmaceutical, and healthcare, consumer goods, and others, widely use CAD and 3D design-based tools in their development processes.
DLT Solutions
Digital Design, IT Perspective, News, Technology, Tips and How-Tos, Uncategorized
The CAD and digital design sector is vast and growing at breakneck speed. It’s expected to reach $11.21 billion by 2023.
Many end-use industries such as automotive, aerospace, entertainment, industrial machinery, civil and construction, electrical and electronics, pharmaceutical, and healthcare, consumer goods, and others, widely use CAD and 3D design-based tools in their development processes.
DLT Solutions
CAD General, Digital Design, IT Perspective, Technology, Uncategorized
Aside from developing one of the sought after building information modeling (BIM) software in the industry today, you’ve got to hand it to the Revit product managers over at Autodesk—they listen.
Grace_Bergen
Cybersecurity, IT Perspective, News, Technology
Symantec’s 2018 Internet Security Threat Report is here. Based on data collected by Symantec’s massive security infrastructure (the largest civilian threat collection network in the world), the report has become the de facto standard for giving enterprises and public organizations essential information to help secure their systems effectively.
By the nature of the topic, the report isn’t an easy read. Expect to be perturbed. However, the insights provided into today’s rapidly evolving threat landscape are invaluable.
DLT Solutions
CAD General, Digital Design, Technology, Uncategorized
Whether you’re a civil engineer, CAD manager, or anyone working on a digital design project, one thing is certain – you’re never the sole collaborator in the process. Contractors, AEC firms, field personnel, even facilities managers, have their hands in the mix too. And that creates a problem for version control and the potential for incorrect information in the field. How do you know you’re working with the most current information? If you’re using traditional non-digital workflows, it’s a problem you likely encounter once too often.
DLT Solutions
Cloud Computing, Cybersecurity, Data, IT Perspective, News, Technology, Uncategorized
Another day, another government ransomware victim. On March 22nd, 2018, the city of Atlanta found itself locked out of computers across government offices and facing a ransom demand of $51,000 or $6,800 per computer, GCN reported.
DLT Solutions
Cloud Computing, Cybersecurity, Data, IT Perspective, News, Technology, Uncategorized
Another day, another government ransomware victim. On March 22nd, 2018, the city of Atlanta found itself locked out of computers across government offices and facing a ransom demand of $51,000 or $6,800 per computer, GCN reported.
DLT Solutions
Digital Design, Technology, Tips and How-Tos, Uncategorized
If you’re fairly new to Autodesk Revit and looking for ways to quickly get up to speed, Autodesk put together a great webinar that offers tips and tricks to get the most out of your user experience. Topics included:
• How does it differ from AutoCAD?
• What do I need to know to get started?
• What are some best practices for working in Revit?
• What are families and how do I use them?
• Where to learn more and how to get support when problems happen
Grace_Bergen
Cybersecurity, IT Perspective, News, Technology
Ransomware is quickly becoming the favored means for criminals to extract a profit from unsuspecting villains – most notably in the public sector. Throughout 2017 ransomware grabbed the headlines – WannaCry, Petya, etc. – both of which targeted government agencies. When they succeed the implications can be serious.
DLT Solutions
Cybersecurity, Infrastructure, Technology, Uncategorized
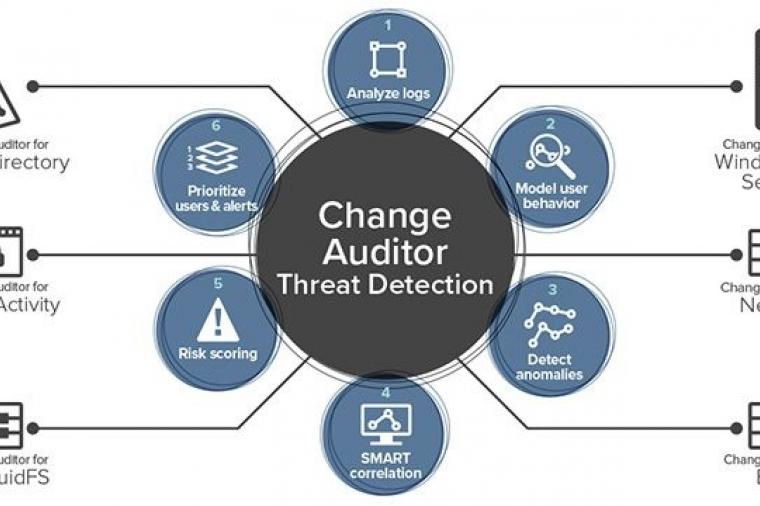
Microsoft Active Directory is a critical tool that helps system administrators manage user privileges and secure their IT infrastructure, yet Active Directory presents several security challenges. Most problematic is that Active Directory’s attack surface is huge. Targets for attack include every domain name user account, admin and security group, domain controller, backup, admin workstation, and admin delegations and privileges. If any one of these targets is compromised, your entire Active Directory can be compromised too.
The Threats
BradleyGernat
Cybersecurity, Infrastructure, IT Perspective, Technology, Uncategorized
Microsoft Active Directory is a critical tool that helps system administrators manage user privileges and secure their IT infrastructure, yet Active Directory presents several security challenges. Most problematic is that Active Directory’s attack surface is huge. Targets for attack include every domain name user account, admin and security group, domain controller, backup, admin workstation, and admin delegations and privileges. If any one of these targets is compromised, your entire Active Directory can be compromised too.
The Threats
BradleyGernat
Cloud Computing, Uncategorized
Are you thinking of moving your databases to the cloud? Perhaps, you’re thinking about transitioning to database-as-a-service (DBaaS)? But what’s involved? What hurdles must be overcome and how do you chart a path to cloud migration of your most sensitive workloads?
Why Move Databases to the Cloud?
Migrating to the cloud offers several benefits to public sector database administrators (DBAs).
BradleyGernat
News
US appoints First Exec Federal Cybersecurity Head
MayaSmith
News, Uncategorized
Declining Spending Begins to Bounce Back with Rising Budgets
Over the past six years, we’ve seen a decline in government spending. But recently, there was been an increase in contract spending that is predicted to continue into fiscal year 2017. According to a study by Bloomberg Government, 60 percent of government spending is consistently on services; knowledge-based services, facility-related services, and technology services. The largest product spending is on technology equipment, with aircraft spending in second.
MayaSmith
News, Uncategorized
Declining Spending Begins to Bounce Back with Rising Budgets
Over the past six years, we’ve seen a decline in government spending. But recently, there was been an increase in contract spending that is predicted to continue into fiscal year 2017. According to a study by Bloomberg Government, 60 percent of government spending is consistently on services; knowledge-based services, facility-related services, and technology services. The largest product spending is on technology equipment, with aircraft spending in second.
MayaSmith
News, Uncategorized
NSA Use of Software Flaws for Hacking Posed Risk to Cybersecurity
Recently, the Nation Security Agency’s (NSA) hacking tools were leaked to the public, exposing many vulnerabilities across the internet and putting companies at risk of data breaches. Many say that the NSA should have disclosed each vulnerability as soon as they discovered it so that they could be fixed. Software vendors like Cisco, Juniper and Fortinet are actively working with their customers to ensure that any flaws in their systems are fixed immediately.
MayaSmith
News, Uncategorized
NSA Use of Software Flaws for Hacking Posed Risk to Cybersecurity
Recently, the Nation Security Agency’s (NSA) hacking tools were leaked to the public, exposing many vulnerabilities across the internet and putting companies at risk of data breaches. Many say that the NSA should have disclosed each vulnerability as soon as they discovered it so that they could be fixed. Software vendors like Cisco, Juniper and Fortinet are actively working with their customers to ensure that any flaws in their systems are fixed immediately.
MayaSmith
News, Uncategorized
DNC Creates Cybersecurity Advisory Board Following Hack
Following the WikiLeak email dump right before the Democratic National Convention (DNC), the Democratic National Committee is creating a cybersecurity advisory board consisting of four industry experts. The board will be responsible for preventing future attacks on the DNC and making sure its cybersecurity capabilities are up-to-par. The committee will also ensure that those whose data was stolen will be protected so that further information from their accounts does not get leaked.
MayaSmith
News, Uncategorized
DNC Creates Cybersecurity Advisory Board Following Hack
Following the WikiLeak email dump right before the Democratic National Convention (DNC), the Democratic National Committee is creating a cybersecurity advisory board consisting of four industry experts. The board will be responsible for preventing future attacks on the DNC and making sure its cybersecurity capabilities are up-to-par. The committee will also ensure that those whose data was stolen will be protected so that further information from their accounts does not get leaked.
MayaSmith
News, Uncategorized
The Most Critical Skills Gap: Cybersecurity
Since Target’s hack back in 2013, cybersecurity has been top of mind for organizations, especially those with sensitive information. However, the talent pool of those who are skilled in intrusion detection, secure software development and attack mitigation is not growing at the same rate as the demand. Many reasons contribute to this disconnect, including a lack of training in higher education and a 53% increase in need.
MayaSmith
News, Uncategorized
The Most Critical Skills Gap: Cybersecurity
Since Target’s hack back in 2013, cybersecurity has been top of mind for organizations, especially those with sensitive information. However, the talent pool of those who are skilled in intrusion detection, secure software development and attack mitigation is not growing at the same rate as the demand. Many reasons contribute to this disconnect, including a lack of training in higher education and a 53% increase in need.
MayaSmith
News, Uncategorized
Technology Is Monitoring the Urban Landscape
MayaSmith
News, Uncategorized
Technology Is Monitoring the Urban Landscape
MayaSmith
News, Uncategorized
Posing as Ransomware, Windows Malware Just Deletes Victims’ Files
MayaSmith
News, Uncategorized
Posing as Ransomware, Windows Malware Just Deletes Victims’ Files
MayaSmith
Uncategorized
It's finally here!
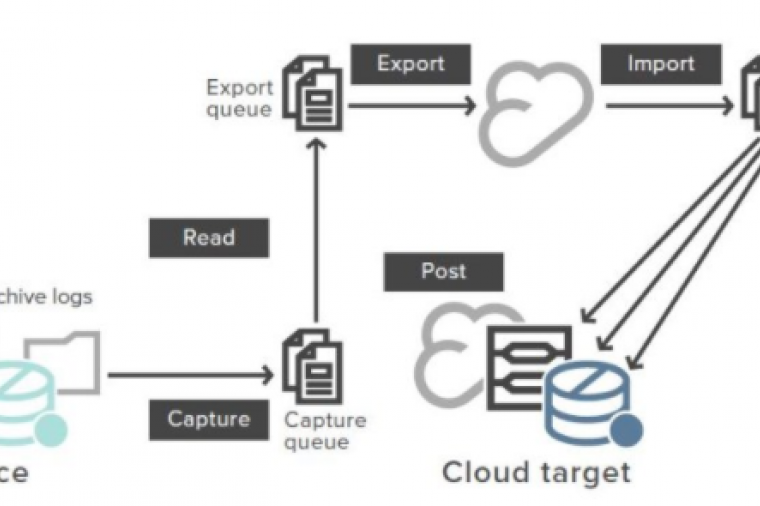
Amazon Web Services (AWS) just announced that the Elastic File System (or "EFS") is a live production service. The service is provisioned out of three regions currently: US-EAST-1, US-WEST-2, and EU-WEST-1.
EFS was originally announced over a year ago at AWS re:Invent in 2015. By AWS standards, the service has been in "preview" for quite some time. I'll admit to you, I was getting a little skeptical that it was going to make it out of preview, but hey, it's good to be wrong sometimes.
Chris Uttenweiler
Digital Design, Uncategorized
The dog days of summer are officially here. So what better time to brush up on your digital design skills. Here are some options for getting ahead of the curve this summer.
Grace_Bergen
News, Uncategorized
Can Cybersecurity Insurance Improve Threat Management?
Following the Brussels, Belgium terrorist attacks back in March, the U.S. House Homeland Security Cybersecurity Subcommittee met to discuss cyberinsurance and how to better promote cybersecurity best practices in general. Many are still questioning whether cyberinsurance will help solve the problem of threat, but the Department of Homeland Security believes it can, by acting as an incentive for better security practices within agencies.
MayaSmith
News, Uncategorized
Can Cybersecurity Insurance Improve Threat Management?
Following the Brussels, Belgium terrorist attacks back in March, the U.S. House Homeland Security Cybersecurity Subcommittee met to discuss cyberinsurance and how to better promote cybersecurity best practices in general. Many are still questioning whether cyberinsurance will help solve the problem of threat, but the Department of Homeland Security believes it can, by acting as an incentive for better security practices within agencies.
MayaSmith